I assume that all of us had the same experience at least once: came to a Microsoft Intune (or EMS) project, and have to create all of the office mobile apps for Android and iOS manually on the SCCM console by our own. But this work was a really mess. Because, the research for the official links became the first pain, and then we need to provide the icons adjustment (using MS Paint?!) and then to include some description, and so on…
Well, the good news are here: these days are completely done!
For Config Mgr 2012 R2 SP1 (or SP2 if you want to call it) with CU2 (and for 1511 also), Microsoft developed and deploy a new Intune extension that create all of the Mobile Office Applications for Android and iOS. I mean, for other words, with a couple of clicks, we can replace a good amount of wasted time.
Curious? Give a deep dive on the following link:
Well, backing to the SCCM (integrated of course!)
I have to admit that this issue consumed a couple of hours, and due that fact I felt that I to share my experience on it. And to be honest, I spent a lot of time around the console, because accessing to the SQL database was never the thought that I’d in mind.
Recently, my daily routine on the SCCM was: “I’ve only three extensions for Microsoft Intune. Am I missing something?”. In fact I was…

The troubleshooting mindset was always around “My SCCM doesn’t get any extension of Office Mobile Apps”. And, once we’re are talking about “cloud services”, we heard so many times everyone telling us to wait for our SCCM to synchronize through Microsoft Intune connector to get the extensions. And that’s what I did.. and I stuck waiting… but nothing happened.
Just in case, if you ever experience a similar behavior on your customers, keep in mind that this solution is completely out of support and if you can, you should try to figure out in a “better” way because my suggestion is fully around SQL. And I am part of those SCCM guys that never ever touched on SCCM database. An yes, in the end I’d to admit: in my case, my SQL database just had an incorrect value on that.
Note: Again, this is not a supported solution! Don’t even try this on a production environment. Try this on your lab please and take your conclusions!
Sharing my “hands-on-lab” experience
First of all, I run a sql query to get some information about all of my extensions:
select L.Name, F.FeatureID, F.StateID,S.FeatureStateName,F.Flag, F.Error from MDMCFDFeature F join CFDLocalizedMetaData L on F.FeatureID=L.FeatureID join CFDFeatureState S on F.StateID=S.FeatureStateID where L.LocaleID=1033
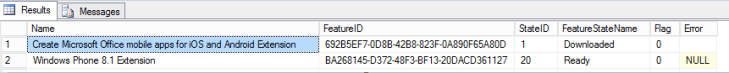
This query returns all of the description names plus the reference ID.
When I saw the results for the first time, I just realized that my Config Mgr really had the extension! But I can’t saw in my console! Confused? This must have an explanation!
So, it’s time to get more information about the specific Extension running the following query:
Select * from CFDMetadata where FeatureID =
‘692B5EF7-0D8B-42B8-823F-0A890F65A80D’
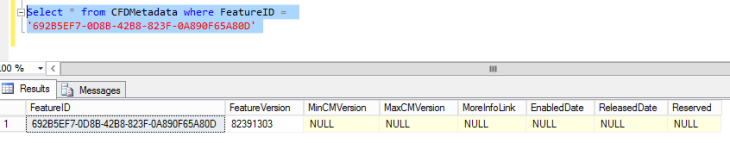
And I found a lot of “NULL” values. So, I’ve tried the update for the specified attribute (by my own of course, and on a lab environment as always):
Be Careful if you really want to do this!
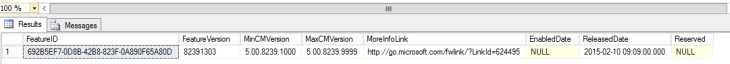
update CFDMetadata
set
MinCMVersion = ‘5.00.8239.1000’,
MaxCMVersion = ‘5.00.8239.9999’,
MoreInfoLink = ‘http://go.microsoft.com/fwlink/?LinkId=624495‘,
ReleasedDate = ‘2015-02-10 09:09:00.000’
where FeatureID =
‘692B5EF7-0D8B-42B8-823F-0A890F65A80D’ and FeatureVersion = 82391303
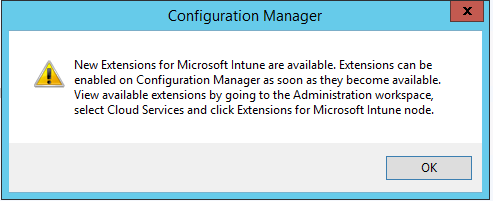
When I restart my console, the Extension pop-up warned me about some extension that I’d available to apply.
And the extension became available.
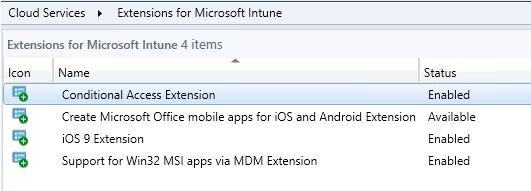
After a couple of minutes…became enabled!
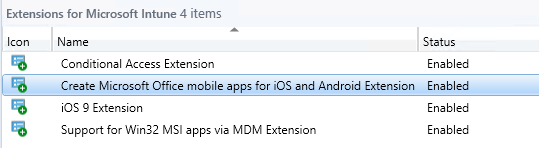
The process will create the office apps automatically.
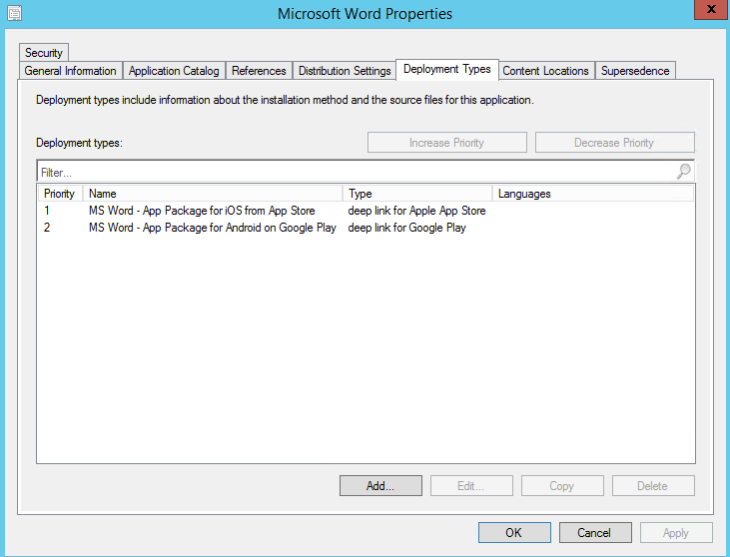
And the “Application Catalog” pane will be full filled also.
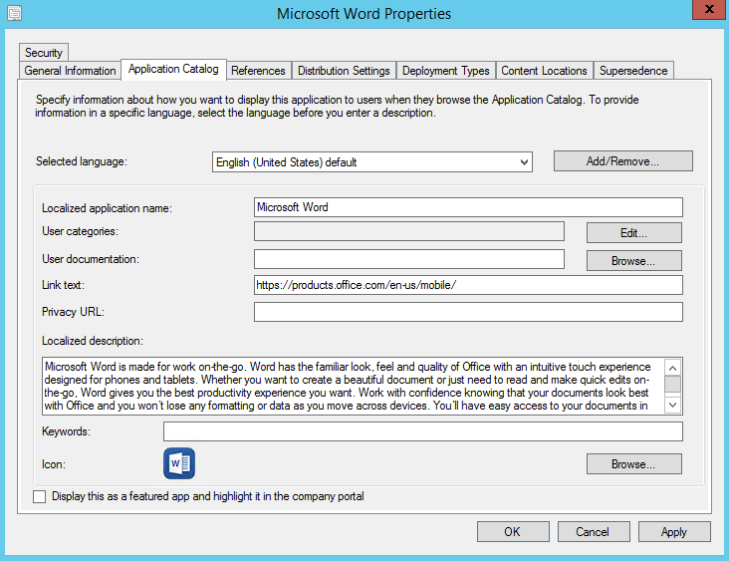
You just have to create your deployments (or advertisements if you want to call it) for your Office Mobile applications/deployment types to your customized users collection. And that’s it!
Enjoy Intune extensions! Enjoy SCCM integrated with Intune!
/ Fabio










































































