Did you asked yourself about both Bitlocker encryption steps provided by ConfigMgr and MDT task sequences? Well, I did. So, when a customer asked me to include BitLocker encryption I made a few research about this theme to understand each of one differences between them. Below, I try to share a few knowledge about it.
ConfigMgr and MDT integrated scenario:
Let’s consider the scenario on having ConfigMgr integrated with MDT as a starting point, since this is the most used scenario in our customers (at least I hope).
For those who use OSD in that way, this is what you’ll find when you create an MDT Task Sequence in your ConfigMgr console:
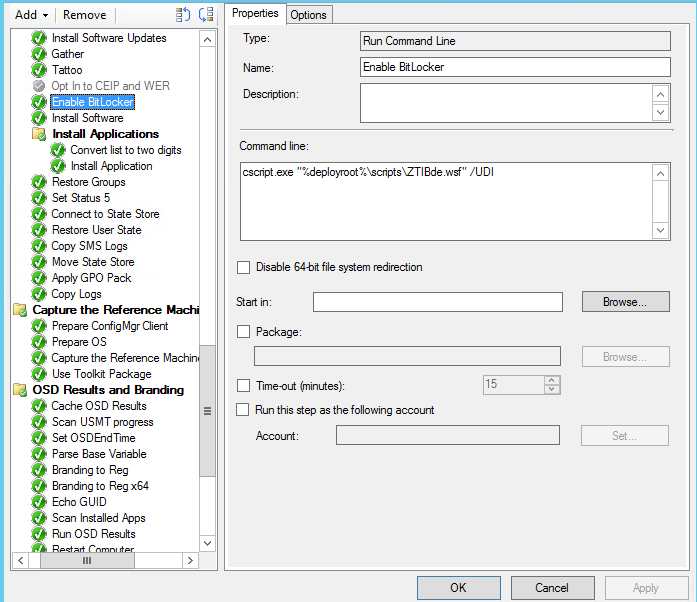
The presented “Enable BitLocker” step is nothing more than an execution of a ZTIBde.wsf script file (executed from the MDT Scripts Package).
The script basically provide a full set of steps (like OS versions, Physical disks, etc.) to validate if the target computer is available for Bitlocker encryption. After performing all validations process, task sequence will start the encryption task using the Windows native tool named “manage-bde.exe” located in the %system32% folder.
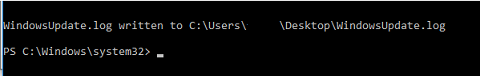
As a last step, the script will place a text file with the Recovery password info into C:\ drive.
Otherwise, if you want to use the native ConfigMgr BitLocker step from Task Sequence, you can add it on the Disks option into the “Add” pane on top of the page.
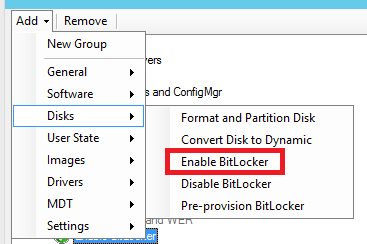
Task Sequence will present the following properties pane as a simple wizard and very similar to the BitLocker page on UDI Wizard.
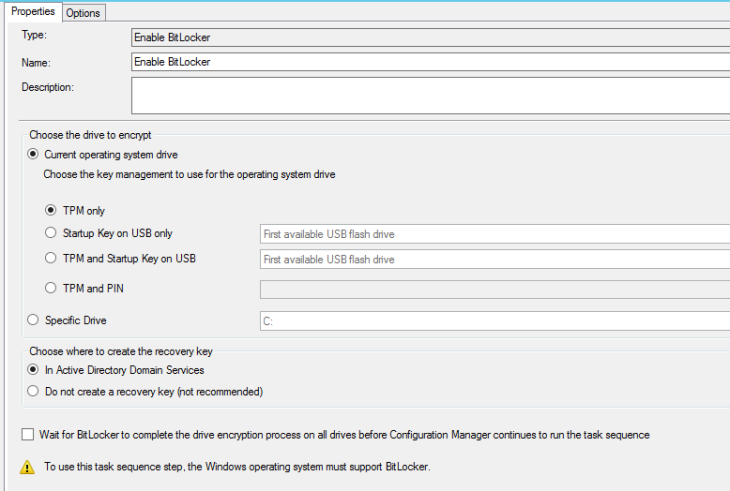
What will be performed here?
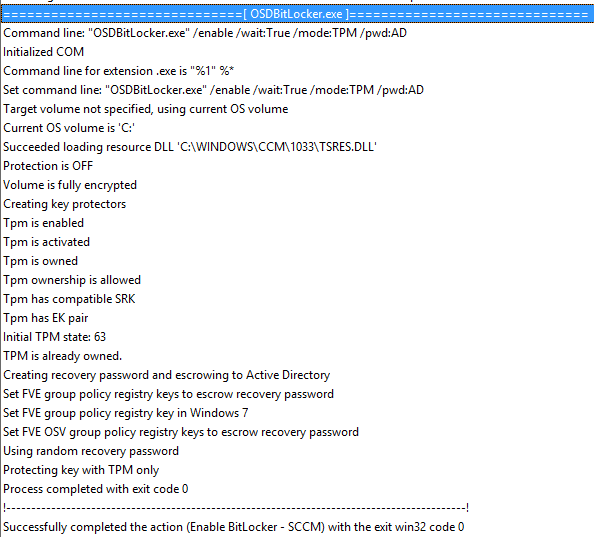
Not so visible like MDT does, but task sequence will run a tool named “OSDBitLocker.exe”. The tool is located into the ConfigMgr installation folder and is copied as a package during OSD process and will do the following steps:
- TPM Validation;
- Create the protectors (Recovery Password);
- OS disk encryption;
- Set the recovery password to AD (if configured).
Diving into smsts.log
MDT Lite Touch:
As you probably know, this is my favorite deployment type. Not only because this is the faster way to deploy customized Operating system images, but is the cleanest and easiest way (with no dependencies) to deploy Windows.
So, when we create a task sequence, this is what we’ll see:
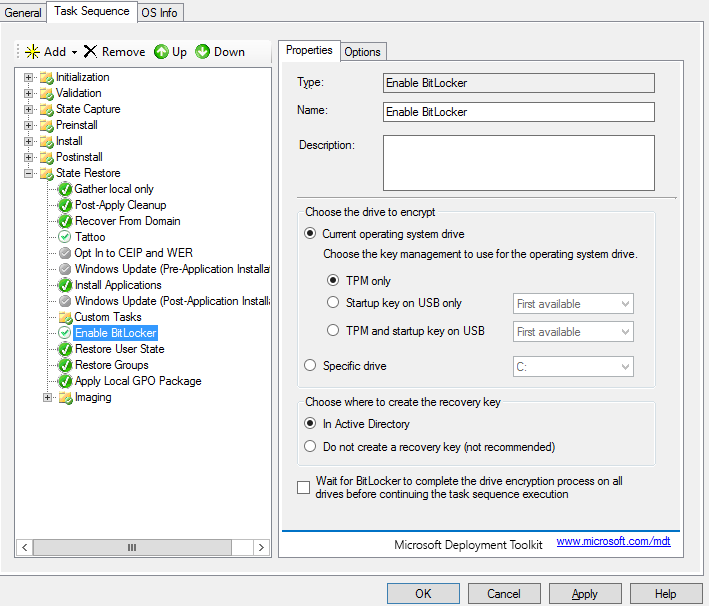
And for options pane, MDT provides us:
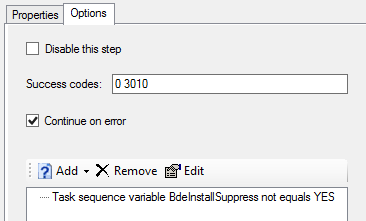
Not difficult to understand, because this is shown in a “Wizard” mode and the variable “BdeInstallSuppress” shouldn’t be YES (via CS.ini or TaskSequence variable).
Additional tip 1:
Since “manage-bde.exe” is a native Windows tool you just can test it in an isolated Laptop/workstation to test it (not with VMs. Check additional tips to understand it better).
In the other hand, if you want to test the OSDBitLocker tool in a completely offline and outside of deployment process, avoiding the wasted deployment duration, just copy the required files and put them in an external USB (for example).
Execute the following command:
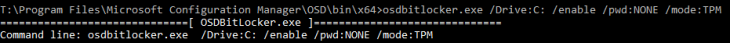
And wait for the BitLocker encryption to be done.
Additional tip 2:
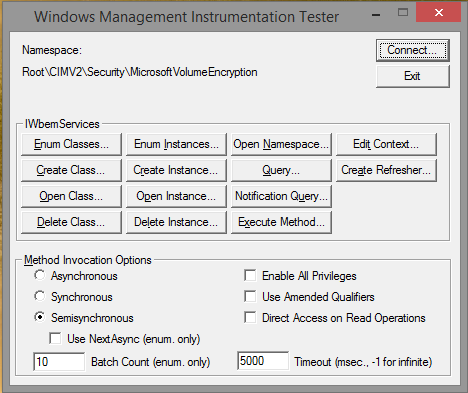
Are you thinking of using this on a VM? You don’t need even to try it. The script will check the physical volumes through WMI and the process is fully explained below.
Namespace: Root\CIMV2\Security\MicrosoftVolumeEncryption
Query: SELECT * FROM Win32_EncryptableVolume
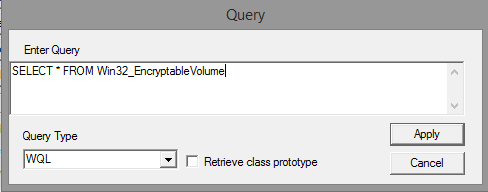
We you select the “Apply” option, it will be shown every encryptable drives in the current machine.
Try it in a virtual machine to see the reason why it fails every time on them. 🙂
Happy deployments!
/ Fabio